Linux Security Guide: How to Investigate Suspected Break-in Attempts in Linux
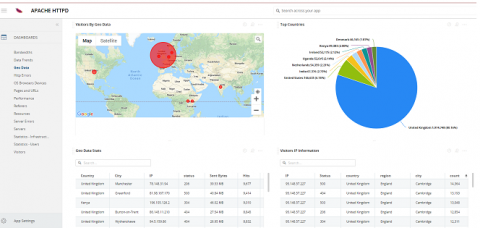
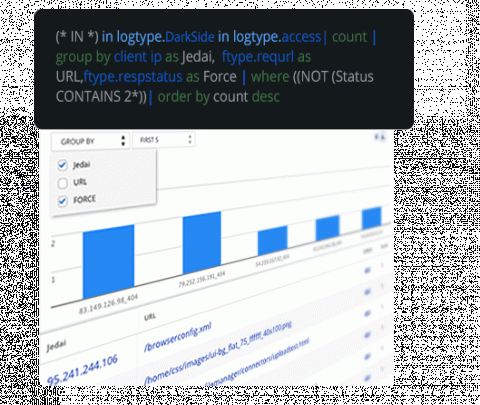
Scenario Linux has a number of built-in tools, commands and files which can track and store information about every user activity. These tools are common in most Linux distributions and can be used to investigate suspicious logins or failed login attempts into the system. In this article, we will talk about some of the initial methods to identify possible security breaches. We will use an Amazon EC2 instance to show these commands.