What is MITRE ATT&CK and How to Use the Framework?
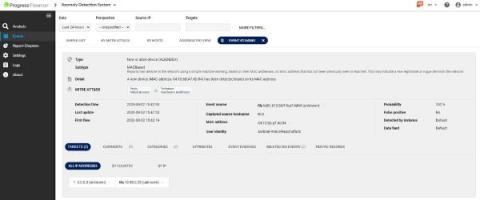
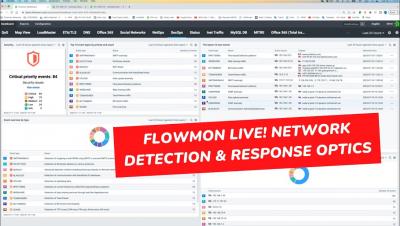
The MITRE ATT@CK® framework is one of the most widely known and used. The Flowmon Anomaly Detection System (ADS) incorporates knowledge of the MITRE ATT&CK framework. Using ADS and its MITRE ATT&CK knowledge makes detecting advanced threats against networks and IT systems easier and simplifies explaining the danger and risks when outlining an attack to all stakeholders.