Operations | Monitoring | ITSM | DevOps | Cloud
Flowmon
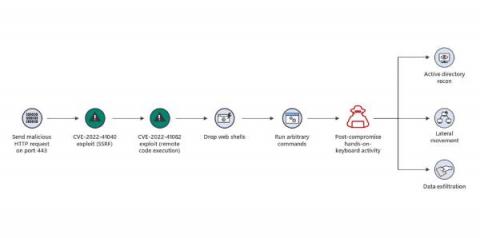
Microsoft Zero-Day Exchange Exploits Show Value of Network Behavior Visibility
There is no end to zero-day attacks. Lessen the pain by spotting them early. In recent days two zero-day vulnerabilities against Microsoft on-premises Exchange Servers have been publicized and exploited. The good news is that Exchange cloud users such as Microsoft 365 customers, need not worry as these exploits are only against the on-premises versions.
Boost Application Experience with Network Behavior Analysis
“Network behavior analysis (NBA) is a network monitoring program that ensures the security of a proprietary network. NBA helps in enhancing network safety by watching traffic and observing unusual activity and departures of a network operation,” explained Techopedia. “Network behavior analysis monitors the inside happenings of an active network by collecting data from many data points and devices to give a detailed offline analysis.
Ransomware: Latest Variants and Trends on the Rise
Here in this blog, we will talk about some of the emerging ransomware you should know about and how you can prevent such attacks.
Application Experience Depends on Your Network Experience
The network is designed to connect the organization’s users, partners, customers and visitors, but those connections are useless without software. While applications run on internal servers, end points and the cloud, the performance of the network in large measure defines the performance of the application, and this performance is what user experience and application experience (AX) is based on.
Find the root cause of slow application experience
Slow App? Where's the Problem?
The reasons that cause applications to run slowly are many and varied. Narrowing down the cause behind any particular instance is time-consuming if the correct network monitoring tools are not in place. The delay in finding a root cause and fixing it always has a negative impact on users of the affected applications.
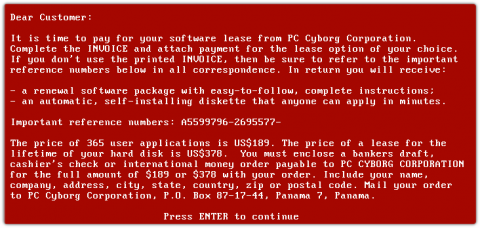
Battle the Ransomware Scourge with Deep Network Insight
Ransomware is the gift that keeps on giving. Old as it is (33 years) ransomware is constantly morphing into new exploits. The reason is simple. Ransomware works and too often cybercriminals walk away with bags of money (or piles of Bitcoin, anyway). “Following the World Health Organization's AIDS conference in 1989, Joseph L. Popp, a Harvard-educated biologist, mailed 20,000 floppy disks to event attendees.