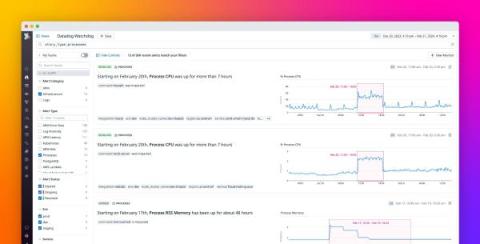
Reduce context switching while troubleshooting with Datadog's IDE plugins
Visibility into the production performance of code iterations helps developers verify that application releases and updates are working as intended. However, when variables such as large-scale user requests and increased server load create issues that were absent during testing, developers will often need to pivot from investigating production data back to their coding environment to address errors and vulnerabilities.