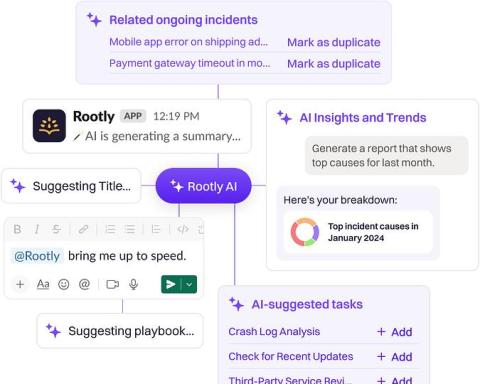
Building a Privacy-First AI for Incident Management
At Rootly, we're integrating AI into incident management with a keen eye on privacy. It's not just about tapping into AI's potential; it's about ensuring we respect and protect our customers’ privacy and sensitive data. Here's a quick overview of how we're blending innovation with strong privacy commitments.