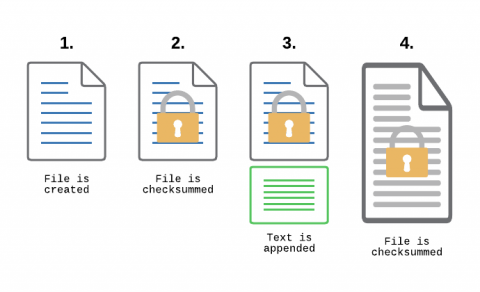
SIEM Tools: For Enhanced Threat Intelligence and System Security
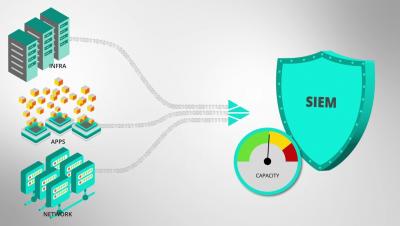
SIEM is an overarching mechanism combining Security Event Management (SEM) and Security Information Management (SIM). It is a combination of different tools such as Event Logs, Security Event Logs, Event Correlation, SIM etc. These work in tandem to provide you an up-to-date threat intelligence infrastructure and enhanced security for your applications and hardware.