Advanced Access Controls with Mattermost Enterprise Edition
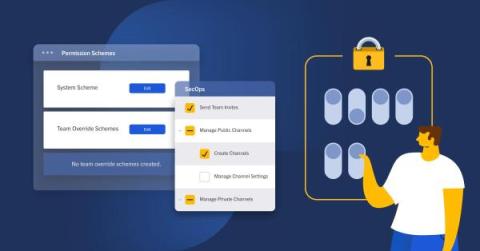
While some smaller companies may only need to use standard access controls to shore up systems, large organizations — particularly those with strict security, confidentiality, and compliance requirements — often require advanced functionality that gives them more authority over which users can access what systems and when.