Cybersecurity Risk Management: Introduction to Security Analytics
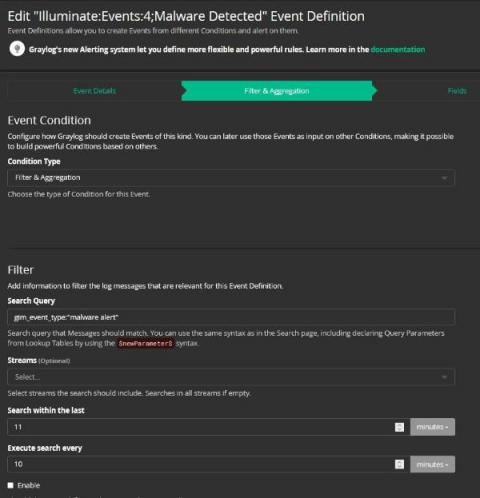
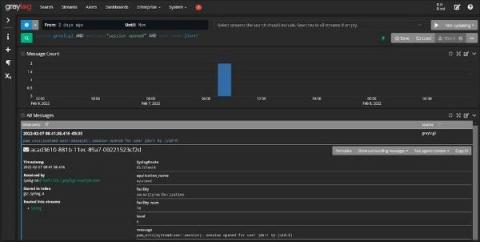
It’s mid-morning. You’re scanning the daily news while enjoying a coffee break. You come across yet another headline broadcasting a supply chain data breach. Your heart skips a quick, almost undetectable, beat. You have the technology in the headline in your stack. You set aside your coffee and begin furiously scanning through the overwhelming number of alerts triggered across all your technologies.