Operations | Monitoring | ITSM | DevOps | Cloud
SIEM
Cut costs, increase storage with InTrust and SIEM integration
How to Overcome the Drawbacks of SIEM Tools
These days, “SIEM” (Security Information and Event Management) is all over the place. SIEM tools work by collecting data from multiple systems and noticing patterns in the data. This adds immediate value to the business by providing insights, security recommendations, and actionable intelligence. Despite being helpful tools for many companies, SIEM tools do have their drawbacks. This article will describe the four main ones and offer suggestions for how they might be overcome.
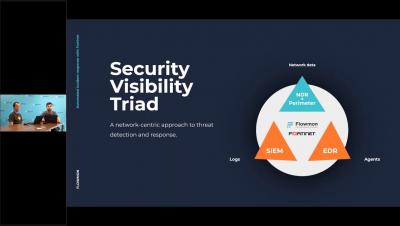
Automated incident response with Flowmon and FortiGate
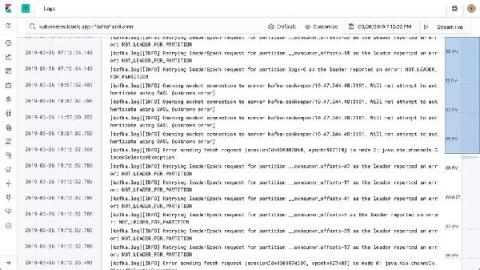
Getting started with adding a new security data source in your Elastic SIEM: Part 1
What I love about our free and open Elastic SIEM is how easy it is to add new data sources. I’ve learned how to do this firsthand, and thought it’d be helpful to share my experience getting started. Last October, I joined Elastic Security when Elastic and Endgame combined forces. Working with our awesome security community, I’ve had the opportunity to add new data sources for our users to complement our growing catalog of integrations.
Virtual Meetup: SIEM 101: What, Why & How of Information Security
A Journey of Elastic SIEM: Getting Started through Threat Analysis Part 1
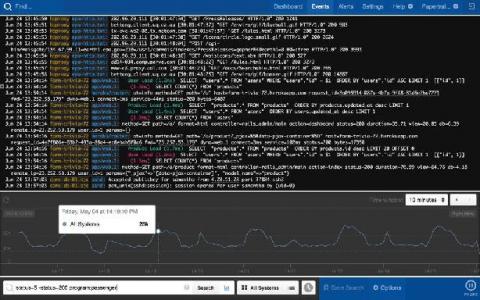
5 Reasons You Should Start Analyzing Your Logs
Integration and Shipping Okta Logs to Logz.io Cloud SIEM
Company security usually depends on your ability to come up with a diverse set of passwords and then manage them. Remembering all of them is considered a tad too difficult for most mere mortals, so a number of password storage apps have emerged. But they too have to be secured, and ultimately results in inefficient access and flawed security. Single-sign on (SSO) is still preferred, but to make it effective, companies like Okta have to secure integration across a number of apps.