Operations | Monitoring | ITSM | DevOps | Cloud
Cyberattacks
Statistics on Cyber Terrorism Attacks and Computer Security Costs
Three Ways a Proactive Defense Strategy Can Prevent Cyberattacks
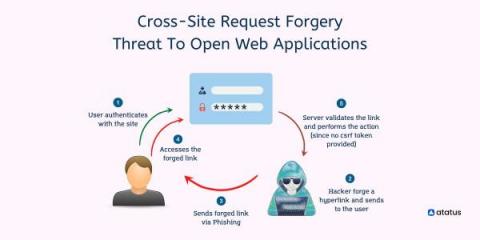
Cross-Site Request Forgery - Threat To Open Web Applications
Cross-site request forgery (CSRF) is an attack that tricks a user's browser into sending a malicious HTTP request to another website. This malicious HTTP request looks like it was sent by the user, but it actually comes from the attacker. A cross-site request forgery (CSRF) attempts to execute a change rather than trying to download personal data. Once an attack is executed there is no way for the attacker to directly monitor the result so attackers often execute multiple forgeries.
Seven steps to help protect your ERP system against cyberattacks
Many companies’ enterprise resource planning systems, which house their most valuable data, are still too vulnerable. What would happen if your enterprise resource planning (ERP) system were attacked? For many companies, the consequences would be devastating.
Prevent XSS attacks with browser testing
Security is a never-ending battle on the web. You can have a server up in just a few minutes, and the next minute, someone is already trying to hack into it. These attacks could be automated using malicious bots or launched manually. Websites can be targeted by a malicious user trying to compromise your web presence or data. Cross-site scripting (XSS) is just one type of attack your site may be vulnerable to.
Seven steps to help protect your ERP system against cyberattacks
What would happen if your enterprise resource planning (ERP) system were attacked? For many companies, the consequences would be devastating. ERP systems not only contain the crown jewels of the business—customer data, stock levels, order entries, production plans, and contract data—they also manage such essential financial processes as order to cash (OTC), and operational processes such as production planning and steering and cash collection and payments.
Anatomy of a Supply Chain Attack Detection and Response
Why Enterprises Need to Prepare for Russian Cyberattacks - and Four Ways to Do It
The invasion of Ukraine has been difficult to watch, and unimaginable to live through. While the primary global focus is, as it should be, on peace and safety, it’s also critical for enterprises to prepare for the likely inevitable Russian cyberattacks.
What Should I Know About Defending IoT Attack Surfaces?
The Internet of Things needs to be part of the overall corporate information security policy to prevent adversaries from using these devices as an entry point. There are several reasons why it’s critical for organizations to defend their IoT attack surface, most importantly being that IoT devices are powerful systems containing compute, storage, and networking that threat actors view as the easiest way to breach an organization or enable exploits.