Adding action links to Oh Dear email notifications
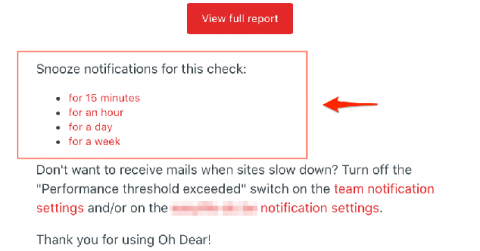
Last week, we improved the email notifications sent by Oh Dear whenever something is down or broken. They now contain links that allow you to snooze further emails, essentially "silencing" the alert for a defined period of time.