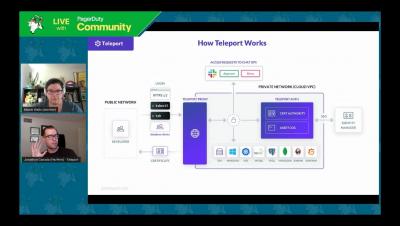
What is Forensic Analysis and Why is it Important for the Security of Your Infrastructure
With the advent of cybercrime in recent years, tracking malicious online activities has become imperative for protecting operations in national security, public safety, law and government enforcement along with protecting private citizens. Consequently, the field of computer forensics is growing, now that legal entities and law enforcement has realized the value IT professionals can deliver.