Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
kOps adds support for Calico's eBPF data plane
Kubernetes operations (kOps) is one of the official Kubernetes (K8s) projects. The kOps project allows for rapid deployment of production-grade K8s clusters in multiple cloud platforms. By leveraging yaml manifests, kOps delivers a familiar experience to users who have worked with kubectl. Similar to K8s clusters in popular cloud platforms, kOps helps set up self-managed clusters to easily deliver high availability.
Resilient Infrastructure for a Secure Future
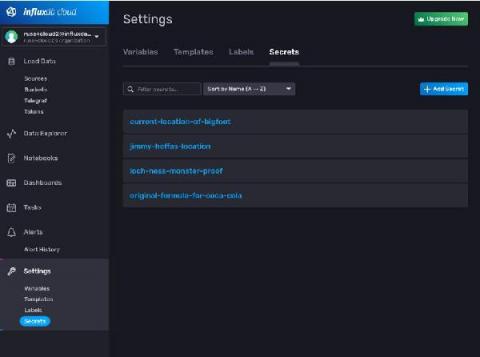
Managing Secrets in the Browser in InfluxDB Cloud
Directly embedding passwords and API keys into the code you write is a bad practice. Of course, everyone knows this, but I’ll be the first to admit that it still happens now and then. In the world of source control and shared codebases, leaking a password can be a huge problem that costs your team time and money. Of course, today many companies leverage a secrets management system to lower the probability of something like this happening.
How VMware Tanzu SaaS Products Handle Data Privacy and Security
Companies today are adopting software as a service (SaaS) at a rapid pace. There are many factors contributing to this trend, including: Many large enterprises, particularly in banking and financial services, have been hesitant to adopt SaaS because it challenges existing risk management models already in place for software.
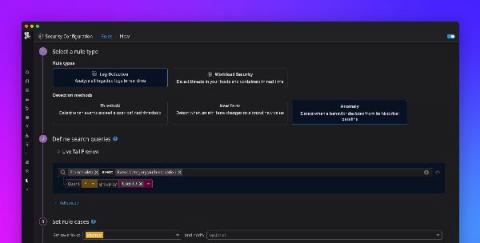
Detect security threats with anomaly detection rules
Securing your environment requires being able to quickly detect abnormal activity that could represent a threat. But today’s modern cloud infrastructure is large, complex, and can generate vast volumes of logs. This makes it difficult to determine what activity is normal and harder to identify anomalous behavior. Now, in addition to threshold and new term –based Threat Detection Rules , Datadog Security Monitoring provides the ability to create anomaly.
Adapting to New Federal Regulations on Cybersecurity and Log Management
The Biden administration signed an executive order recently to regulate security practices among federal agencies and establishments. The decision modernizes and improves government networks in pursuit of fool-proof federal cyber defense. This comes in the wake of a series of malicious cyberattacks that targeted both public and private entities in the past year. In the largest breach in US history, SolarWinds
7 Ways To Amp Up Website Security Without Ditching Great UX Design
Technology has paved the way for businesses to reach out to more customers and clients. One of the most effective ways to reach more people is through the Internet, by creating a great website. Nowadays, businesses with websites have a name and face in the online world. However, as technology advances, so do security risks. If hackers get into a website, they can steal sensitive data – say, customer information (i.e., payment methods, addresses, etc.).
Highlights from Black Hat USA 2021
Black Hat USA is one of the industry’s oldest and most well-established security events. Last year, the conference was held virtually for the first time in its history. This year’s conference brought together the best of both worlds, with a hybrid event that was held virtually and in person in Las Vegas. Historically, Black Hat has seen about 20,000 attendees at its in-person conference.