Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
What's Important in 2021? - Bold Predictions in the Digital Workplace and Delivering Security with a Remote Workforce
At Ivanti, our highest priority is our customer. With that in mind, I thought it would be a good idea to share some research that my team and I have found valuable as we have migrated through the COVID period. The two pieces of Gartner research, highlighted below and linked to on our landing page below, really hit home at Ivanti so we wanted to share them with all of you.
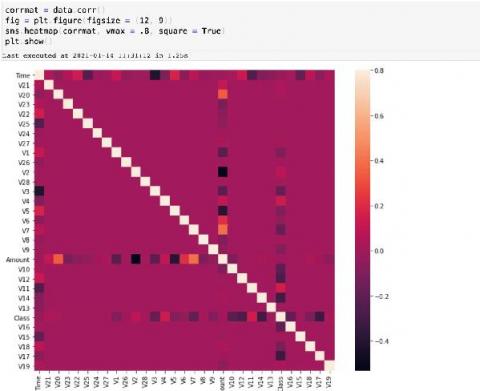
Detecting Credit Card Fraud Using SMLE
Organizations lose billions of dollars to fraud each year. For instance, the financial services sector projects losses to reach $40 billion per year in the next 5-7 years unless financial institutions, merchants, and consumers become more diligent about fraud detection and prevention. Splunk delivers integrated enterprise fraud management software that quickly defines behavior patterns and protects enterprise information from malicious actors.
Private home directories for Ubuntu 21.04
Ubuntu has evolved a lot since its early beginnings as an easier-to-use derivative of Debian that catered primarily to the nascent Linux desktop market. Today Ubuntu is deployed beyond just your laptops at home and in the office. Nowadays you are more likely to find Ubuntu in the cloud, powering some of the world’s best known enterprises and running on various IoT devices out in the field.
Calico Enterprise Multi Cluster Management - Federated Identity and Services
How to implement CFEngine custom promise types in bash
This blog post will focus on the bash programming part of implementing a promise type. To understand what custom promise types are, and how to use them, you should read the introduction first.
Applying Strong Cyber Hygiene Security to IoT Endpoints
The Internet of Things, better known as IoT. You’ve heard of it, right? But do you know what it is? Simply, it is the interconnection of things (or endpoints) on the Internet to send and receive data. Today, experts calculate that there are 31 billion things connected to the insecure Internet, and growing exponentially. Did you know there are different types of IoT applications?
How We Use InfluxDB for Security Monitoring
At InfluxData, we believe it makes sense to use a time series database for security monitoring. In summary, it’s because security investigations are inevitably time-oriented — you want to monitor and alert on who accessed what, from where, at which time — and time series databases like InfluxDB are very efficient at querying the data necessary to do this.
How to detect sudo's CVE-2021-3156 using Falco
A recent privilege escalation heap overflow vulnerability (CVSS 7.8), CVE-2021-3156, has been found in sudo. sudo is a powerful utility built in almost all Unix-like based OSes. This includes Linux distributions, like Ubuntu 20 (Sudo 1.8.31), Debian 10 (Sudo 1.8.27), and Fedora 33 (Sudo 1.9.2). This popular tool allows users to run commands with other user privileges.