Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
Shipping Sysmon Logs to Logz.io Cloud SIEM
System Monitor (Sysmon) is Windows’ service for monitoring activity and recording it to the Windows event log. It is the go-to for logging anything on a PC. Sysmon will immediately log events, capturing vital info. The driver for Sysmon will install as a boot-start driver, enabling capture of any and all events from the get-go. Now, you can send Sysmon logs straight to Logz.io Cloud SIEM.
Zero trust network security for Kubernetes with Sysdig
Troubleshooting Kubernetes Networking with Calico
The Technology Companies Think They Can Live Without (and Why They're Wrong)
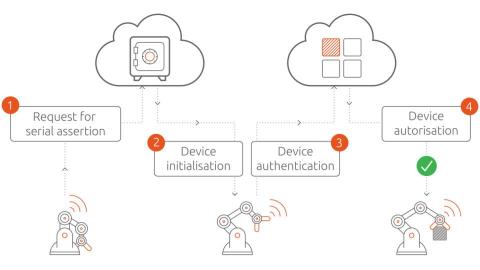
Cybersecurity defenses for IIoT
Cybersecurity attacks on industrial IoT solutions can have detrimental consequences. This is the case because IoT devices record privacy-sensitive data and control production assets. Therefore, demonstrable trustworthiness is prerequisite to IoT adoption in industrial settings. Fortunately, IT security is a mature field. Experts have identified classes of threats devices may be subject to. Let’s discuss these threat patterns and mitigation strategies in the IIoT context.
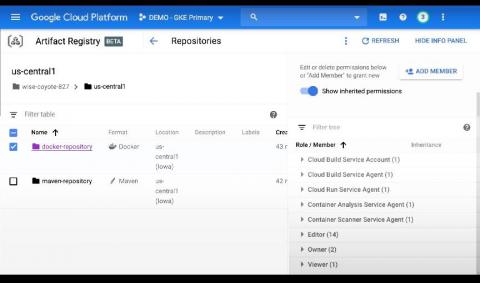
Sysdig extends image scanning to Google Cloud's Artifact Registry
In support of modern application development built on CI/CD, containers and open source, Google Cloud launched Artifact Registry (now generally available), a new artifact management solution. Sysdig helps DevOps teams using Artifact Registry confidently secure the build pipeline with comprehensive image scanning that identifies container vulnerabilities and misconfigurations to reduce risk.