Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
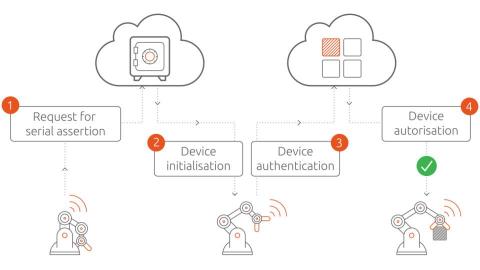
Cybersecurity defenses for IIoT
Cybersecurity attacks on industrial IoT solutions can have detrimental consequences. This is the case because IoT devices record privacy-sensitive data and control production assets. Therefore, demonstrable trustworthiness is prerequisite to IoT adoption in industrial settings. Fortunately, IT security is a mature field. Experts have identified classes of threats devices may be subject to. Let’s discuss these threat patterns and mitigation strategies in the IIoT context.
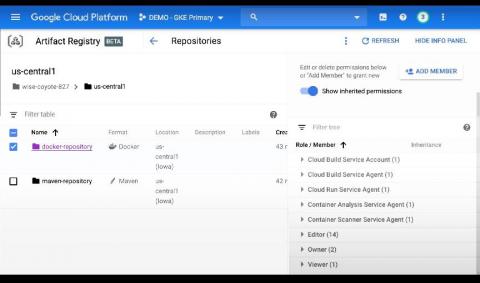
Sysdig extends image scanning to Google Cloud's Artifact Registry
In support of modern application development built on CI/CD, containers and open source, Google Cloud launched Artifact Registry (now generally available), a new artifact management solution. Sysdig helps DevOps teams using Artifact Registry confidently secure the build pipeline with comprehensive image scanning that identifies container vulnerabilities and misconfigurations to reduce risk.
Winning On Tomorrow's Interconnected Battlefields
Getting up and running with Calico on your Rancher Kubernetes Cluster
Quick Intro: Sysdig Secure DevOps Platform
Ivanti Patch Management Technology Enhances XM Cyber's Breach and Attack Simulation (BAS) Platform
In today's press release, we announced the incorporation of Ivanti patch management technology into the XM Cyber BAS platform! XM Cyber is a multi-award-winning leader in breach and attack simulation (BAS) advanced cyber risk analytics and cloud security posture management.
How to monitor Kubernetes control plane
The control plane is the brain and heart of Kubernetes. All of its components are key to the proper working and efficiency of the cluster. Monitor Kubernetes control plane is just as important as monitoring the status of the nodes or the applications running inside. It may be even more important, because an issue with the control plane will affect all of the applications and cause potential outages.
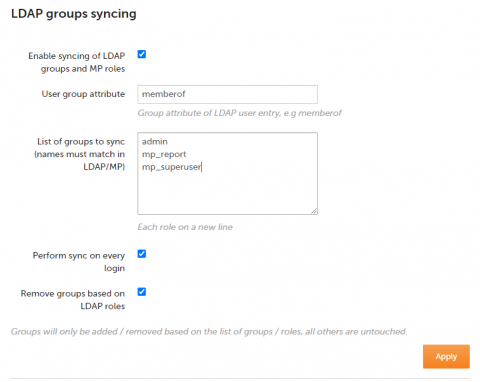
CFEngine 3.12.6 and 3.15.3 released
We are pleased to announce two new patch releases for CFEngine, version 3.12.6 and 3.15.3! These releases mainly contain bug fixes and dependency updates, but in 3.15.3 there are also some new enhancements in Mission Portal. The new cf-secret binary is also included in 3.15.3 packages.