How Log Analytics Improves Your Zero Trust Security Model
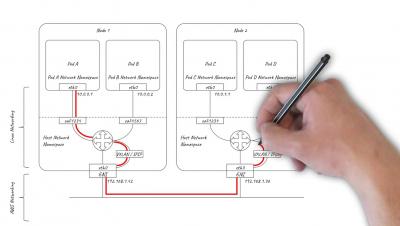
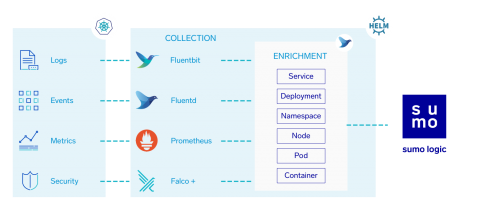
Over the past few years, cloud computing has passed through its hype and early-adopter phases. Now we are hitting the peak of migration from on-premise to cloud-based infrastructure. Consequently, this transition and the advent of cloud computing has dramatically changed the way we think about security. Namely, the security paradigm has shifted towards a Zero Trust Security Model.