Operations | Monitoring | ITSM | DevOps | Cloud
Exigence
How MSPs and MSSPs can reduce risk and liability for their clients
For 83% of companies, a cyber incident is just a matter of time (IBM). And when it does happen, it will cost the organization millions, coming in at a global average of $4.35 million per breach. Add to that stringent data protection laws and the growing frequency and reach of ransomware and other sophisticated attacks.
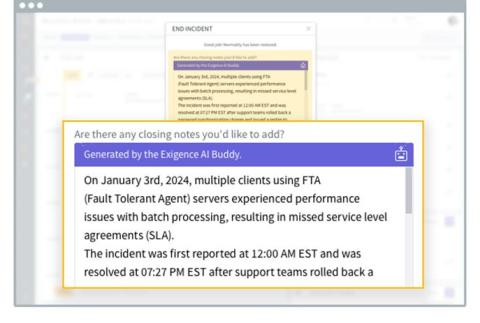
Automate insights-rich incident summaries with generative AI
Does this sound familiar? The incident has just been resolved and management is putting on a lot of pressure. They want to understand what happened and why. Now. They want to make sure customers and internal stakeholders get updated about what happened and how it was resolved. ASAP. But putting together all the needed information about the why, how, when, and who, can take weeks. Still, people are calling and writing. Nonstop.
How generative AI is increasing cyber risk & what to do to make sure you're ready
Generative AI is all the buzz these days with the popularity of platforms and tools such as ChatGPT, Bard, Scribe, Jasper, and others experiencing exponential growth. This is a technology that has come to the fore with the force of a runaway train that’s bringing us head long into the future at the speed of light. It is transforming everything we do from writing code to making travel plans. And cybersecurity is no exception.
How summertime turns up the heat on cyber readiness (and what to do about it)
“Malicious cyber actors aren’t making the same holiday plans as you.” (CISA & FBI) Summertime is prime time for cyberattacks. According to one survey, 58% of security professionals believe that there is seasonality in the attacks that their company experiences every year, with the majority citing summer as high season for breaches.
Why an incident response plan is a security must-have for every organization
“By failing to prepare, you are preparing to fail. Preparation prior to a breach is critical to reducing recovery time and costs.” (RSAConference) For 83% of companies, a cyber incident is just a matter of time (IBM). And when it does happen, it will cost the organization millions, coming in at a global average of $4.35 million per breach. The damage isn’t only financial, nor solely related to customer loyalty and brand equity.
Common Incident Terminology
Operations, customer support, engineers and most groups use inconsistent language. This is a serious problem. Imagine NASA doing that with astronauts or a navy with ships talking to each other, but not using the same terms. Something very bad will happen. In our space of incident management, we use words like broke, failed, outage, doesn’t work, dead…all describing the same condition.
DataScan transforms incident response & business continuity tests
With more than $80 billion of loan collateral in its systems, DataScan is an industry leader in providing solutions for wholesale asset financing and inventory risk management. The company’s InfoSec leadership understood that they needed to take a whole new approach to incident response and to advance its security maturity. Having multiple tools for managing incidents and conducting business was translating into inefficiencies, prolonged resolutions, and stress.
Incident Innovation: ITSM Incident Management vs FEMA Incident Command System - Goals
The FEMA Incident Command System responds to wide area disasters like an earthquake, fire, flood, hurricane, and tornado, while ITIL is used for digital services and applications. In large organizations, there is the facilities team and the data center team. FEMA is associated with the facilities team and ITIL with the smaller data center team. What characteristics are shared between the two and what are the main differences?
A multi-billion-dollar software giant leverages Exigence to improve incident management collaboration & outcomes
A global leader in SaaS-based and on-premise software solutions that power innovative digital experiences was looking to replace the internal tool that was being used for resolving outages, service degradation, data center connection loss, and other incidents.