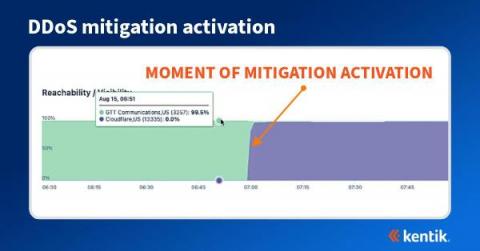
The Latest Ransomware Stats Are In and It's Not Good News.
Out of 10 key metrics tracked quarterly to establish the state of ransomware activity, only one metric stayed static from Q1 to Q3 2022. The other nine all worsened. That’s an alarming trend, especially given that many business leaders hoped to see ransomware activity taper off after a historic surge during the peak of the pandemic. Ivanti, together with Cyber Security Works and Cyware, collaborated on the just-released report.