Tips and Tricks for the Small SOC: Part II
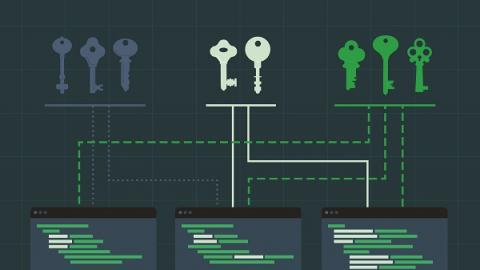
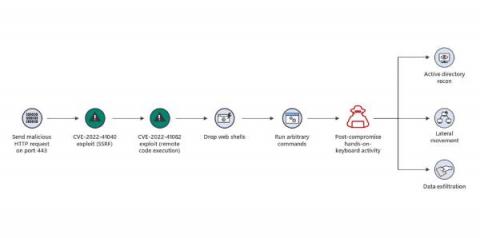
It’s Cybersecurity Awareness Month, and in that spirit, we’re offering a number of tips and tricks small security operations center (SOC) teams can use. I started my career working as part of a small SOC team, and working with other security experts here at Logz.io, we’re happy to offer these to small SOC teams who can often use all the help they can get! In the last post, we talked about managing security talent and building processes.