Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
Do VPNs Really Keep Your Browsing Data Private?
Cloud Security: Indiana Bob's Server Closet Versus Data Centers | Security Insights Podcast, Episode 28
Amanda and Chris share stories proving why your data really is more secure in the cloud than the average on-premises server closet – and what organizations should worry more about when it comes to data security.
Secure Backup Strategies for 2022
Hard drive crash. Ransomware. Equipment failure. Accidental deletion. Theft. There are plenty of reasons why end users want to have a secure and up-to-date backup of their most important files. And there are just as many approaches to backup and recovery as there are reasons to want it in place. In this article, we’ll discuss practical strategies and best practices for backing up important data, including consumer-level options and how to get the most from an enterprise-grade backup solution.
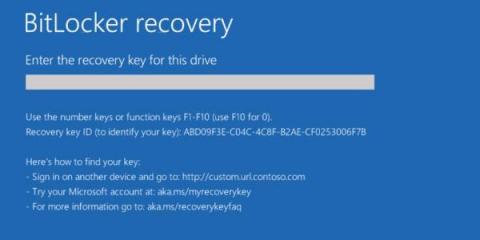
3-Step Approach to Eliminate the BitLocker Recovery Key Backup Issue using Nexthink
In today’s era of “Work from anywhere”, Data Security & Data Encryption has become a vital security step for organisations world-wide and a key component for security compliance. BitLocker is one of the popular Software Stacks for enforcing encryption on all devices & drives. Exponential complexity for managing the encryption compliance and the backup of the recovery keys for all devices in the organization has increasingly become a key challenge for EUC Professionals.
Trending topics at KubeCon + CNC NA 2022
Throughout KubeCon + CloudNativeCon NA 2022, our team was able to speak to over 100 people from the cloud-native community to learn more about their thoughts and experience of the event. This blog will explore what the community thought was the hot topic of discussion at KubeCon + CNC NA 2022, which includes topics such as security, cost, and developer experience. Check out the full video below.
Cribl is Redefining Search for Your Observability & Security Data
Cribl, a leader in open observability, today released Cribl Search, the first federated query engine focused on observability and security data. Search flips the observability market on its head, dispatching queries to where the data is already at rest. Cribl Search was engineered to let you search data-in-place, whether the data remains at the edge, in the stream, in the observability lake, at the endpoint, or even in existing search tools.
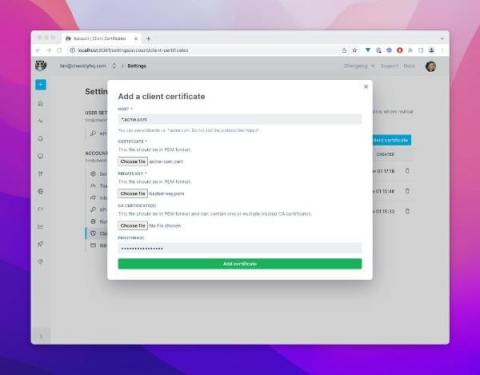
Using Client Certificates for mTLS and Zero Trust Networks
You can now use Checkly to monitor API endpoints secured with TLS Client Certificates. This post dives into why and how you would use client certificates and mTLS (Mutual TLS) in your API infrastructure. Let's go!
Jason Chan on How Automation Transformed Netflix's Cybersecurity Posture
Jason Chan, a key member of the Torq Advisory Board, has spent more than 20 years working in pivotal cybersecurity roles. One of his most important positions was leading the information security organization at the video streaming behemoth Netflix for more than a decade. His Netflix team set the bar extraordinarily high, focusing on sophisticated risk assessment and management, and compliance management strategies and approaches.
Protecting Your VoIP Infrastructure From DDoS Attacks
Distributed denial of service (DDoS) attacks are an ongoing issue for communications service providers, putting critical systems at risk, undercutting service level agreements, and bringing unwanted headlines. In the first half of 2022 6 million of these attacks were reported. Some metrics of DDoS attacks in 1H2022 compared to 2H2021.