Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
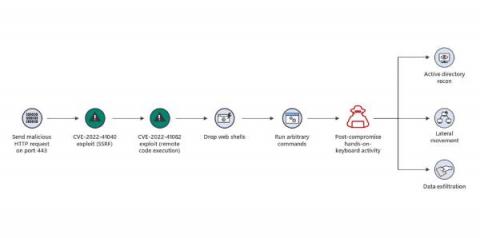
Microsoft Zero-Day Exchange Exploits Show Value of Network Behavior Visibility
There is no end to zero-day attacks. Lessen the pain by spotting them early. In recent days two zero-day vulnerabilities against Microsoft on-premises Exchange Servers have been publicized and exploited. The good news is that Exchange cloud users such as Microsoft 365 customers, need not worry as these exploits are only against the on-premises versions.
Keeping Your Organization Secure with Limited SOC Resources
Organizations face a growing threat from cybercriminals while struggling to find qualified security professionals who can protect their infrastructure and sensitive data. This blog will explore the concept of a Security Operations Center (SOC) and the role of SOC analysts in securing your organization. We will also discuss how your organization can leverage automation to improve SOC effectiveness and fill in the gaps when you cannot support a full staff of security professionals.
How to Put Software Development Security First
What are the keys to building software development security into the early stages of product development? And what are the costs of ignoring security? In this article, xMatters Product Manager Kit Brown-Watts provides his insights on the matter. Every investment decision comes with trade-offs, usually in the form of cost, quality, or speed. The CQS Matrix, as I like to call it, captures the dilemma most product people face.
How To Make A Complete And Thorough Protection For Your Business
Elastic Announces Innovations to Transform the Way Organizations Search, Observe and Protect their Data
Why IT Skills Are Vital When You're Running an eCommerce Business
Tips and Tricks for the Small SOC: Part I
Every security operations center (SOC) team is different, and for smaller teams, even small challenges can seem big. I started my career in cybersecurity as part of a smaller team, and eventually grew into a SOC role. During that time, I gained a good deal of knowledge about the dos and don’ts of what a small SOC team needs to do in order to be successful.
3 Common Misconceptions about Executive Order 14028: Improving the Nation's Cybersecurity
The United States is the #1 target for cybersecurity attacks in the world. 38% of targeted cybersecurity attacks so far in 2022 were aimed at the United States data and systems. That’s alarming. And we see it in the news almost every day. Solarwinds, Colonial Pipeline, The Pulse Secure VPN zero-day… There’s an increasing number of threats and attacks, to the tune of 15.1% year over year.
Automate Calico Cloud and EKS cluster integration using AWS Control Tower
Productive, scalable, and cost-effective, cloud infrastructure empowers innovation and faster deliverables. It’s a no-brainer why organizations are migrating to the cloud and containerizing their applications. As businesses scale their cloud infrastructure, they cannot be bottlenecked by security concerns. One way to release these bottlenecks and free up resources is by using automation.