Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
Cyber Security Mega Breaches: Best Practices & Log Management
While the Capital One breach may have been jaw-dropping in its sheer scale, there are best practice lessons to be learned in its remediation response, says Nick Carstensen, technical product evangelist at Graylog.
11 Different Types of Spoofing Attacks to Be Aware Of
In terms of cyber-attack vectors, spoofing is exactly what it sounds like. This term embraces a series of techniques aimed at masquerading an attacker or electronic device as someone or something else to gain the victim’s confidence. Whether it is used to deceive a user or to manipulate a computer system, this multi-pronged phenomenon is often at the core of social engineering hoaxes in general and phishing campaigns in particular.
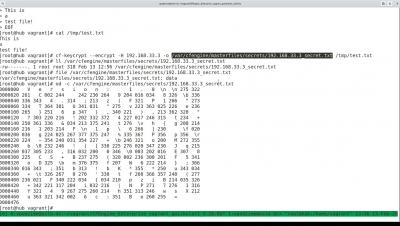
Developer demo: Using cf-keycrypt to encrypt host-specific secrets
Key security functions of unified endpoint management
As part of digital transformation, the adoption of a wide range of devices for work is on the rise. A unified endpoint management (UEM) solution is capable of enforcing management policies and configurations, as well as securing endpoints. In a previous blog, we reviewed the capabilities of a good UEM solution. In this instalment, we look at UEM security features.
Playing defense against Gamaredon Group
For several months, the Intelligence & Analytics team at Elastic Security has tracked an ongoing adversary campaign appearing to target Ukranian government officials. Based on our monitoring, we believe Gamaredon Group, a suspected Russia-based threat group, is behind this campaign. Our observations suggest a significant overlap between tactics, techniques, and procedures (TTPs) included within this campaign and public reporting.
Modernizing the CFEngine Project - Vratislav Podzimek & Ole Herman S. Elgesem (Cfgmgmtcamp 2020)
Supercharging Workload Security in Your K8s Cluster
2019 was a big year for Kubernetes adoption, and 2020 is sure to exceed that pace. Already, we have seen a large number of organizations migrating their workloads to Kubernetes (k8s) both in public and private clouds as they embrace a hybrid cloud strategy. With so much at stake, what are you currently using for network security inside your k8s cluster?
Elastic partners with DDC to offer free election security to 2020 campaigns
We are excited to announce that Elastic will offer free, monitored Elastic Endpoint Security to the 2020 US presidential and congressional campaigns in partnership with Defending Digital Campaigns. Defending Digital Campaigns (DDC) is a non-partisan organization that provides low- and no-cost security products and services to federal campaigns to help defend them from cyberattacks and election interference.
Recovering from OneDrive for Business ransomware attacks
Ransomware has been a growing threat in recent years, and experts now estimate the cost of these attacks at $7.5 billion in the USA alone in 2019. The affected institutions include 966 government agencies, educational establishments, and healthcare providers. Since most ransomware attacks stem from a small mistake made by one end user, either through phishing emails or stolen credentials, the threat is only expected to increase in the years to come.