Threat Hunting With ML: Another Reason to SMLE
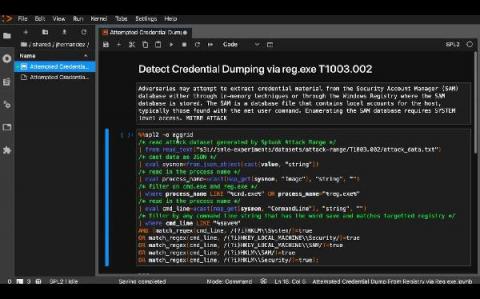
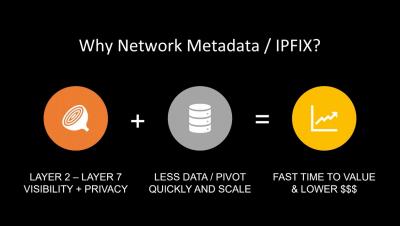
Security is an essential part of any modern IT foundation, whether in smaller shops or at enterprise-scale. It used to be sufficient to implement rules-based software to defend against malicious actors, but those malicious actors are not standing still. Just as every aspect of IT has become more sophisticated, attackers have continued to innovate as well. Building more and more rules-based software to detect security events means you are always one step behind in an unsustainable fight.