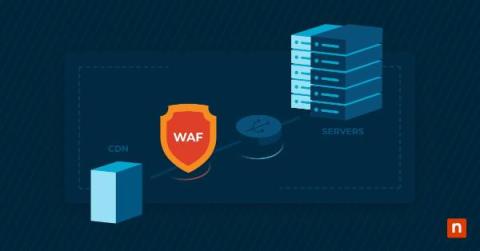
What Is WAF? Web Application Firewall Defined
The rapid evolution of technology has given rise to sophisticated cyber threats that can exploit vulnerabilities in web applications. Cybercriminals continually devise new methods to compromise data integrity, confidentiality, and availability. To counter these threats, organizations must adopt advanced security measures that go beyond traditional security protocols.