Operations | Monitoring | ITSM | DevOps | Cloud
ManageEngine
Five cybersecurity best practices to follow in 2019
Research by Cybersecurity Ventures predicts ransomware alone will cost businesses around the world more than $11.5 billion in 2019. What’s worse, this same study also predicts businesses will experience a cyberattack every 14 seconds by 2019, up from once every 40 seconds in 2016. So what can you do to mitigate the increasing threat of cyberattacks? Here are five IT security best practices that can help.
Getting started with Analytics Plus
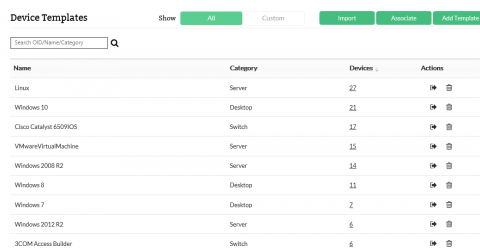
OpManager doubles the number of device templates, cuts your work in half
Just last month we heard flattering statements about OpManager’s UX, and nothing makes us happier than knowing that our continuous improvements have positively impacted our users. We’re always eager to meet your growing IT infrastructure needs, so we’re happy to introduce a set of 4,000 new device templates. That doubles the number of OpManager device templates to over 8,000, helping you in your goal of comprehensive network management.
Automate compliance reporting for all major audits
How to avoid getting tricked by hackers this Halloween
While everyone prepares for the frights of Halloween, there’s a real evil lurking just out of sight—an imminent threat that grows stronger each passing day. And no amount of burning sage, sprinkling salt, or carrying garlic will ward off this threat. Gather around folks, for in October, not only do we celebrate Halloween, but also National Cybersecurity Awareness Month.
Industry best practices for endpoint security
Lately, hackers on the lookout for vulnerable systems have kept the IT industry busy. While various OS and software vendors strive to keep their users’ data intact by providing timely updates, manually securing endpoints by applying these updates is challenging due to factors such as time, staffing, and IT budgets. To help admins out, we’ve compiled a list of some industry best practices you can implement to stay vigilant against cyberattacks and data theft.