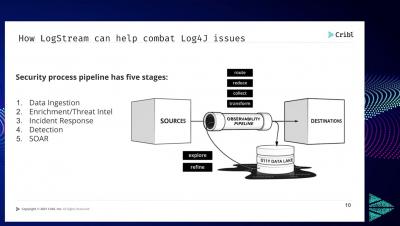
Find and mitigate Log4j vulnerabilities with Puppet Enterprise
Log4j, the popular open-source logging library, had a rough December and closed out the year with an impressive streak of four critical vulnerabilities so far. Many are calling this the worst cybersecurity event in history. Again, so far.