Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
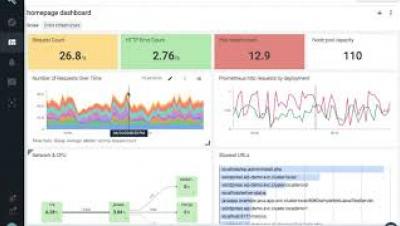
Sysdig Cloud-native Intelligence Platform overview
Falco joins CNCF Sandbox.
Security is a key consideration for any organization seeking to standardize and scale their cloud-native platforms. Falco, the behavioral activity monitoring tool from Sysdig, is becoming a popular option for open source container runtime security on cloud-native platforms built using Kubernetes, Cloud Foundry, and OpenShift.
Introduction to Kubernetes Network Policy with Use Cases
Kubernetes Security Considerations for IDS/IPS in the age of TLS v1.3
Improving Security Forensics in Kubernetes Environments
Tips on Security Risk Assessment
Performing a security risk assessment has become an economic and functional necessity in the digital economy. Cyber-threats and many of the legal and operational aspects of data-handling now constitute as much of a challenge to enterprise success as effective marketing, and continuous service delivery.
Manage mobile devices with KACE Cloud MDM
NIF, World's Largest Laser and Splunk
Simplifying security auditing, part 6: Compliance and the cloud
In part 5, we looked at auditing your network device logs. A decade ago, security professionals were primarily concerned about network perimeter and endpoint security. While those concerns are still valid, technological advancements have created new scenarios that need to be addressed.