Why Grouping Devices Is So Critical for IT Infrastructure Management
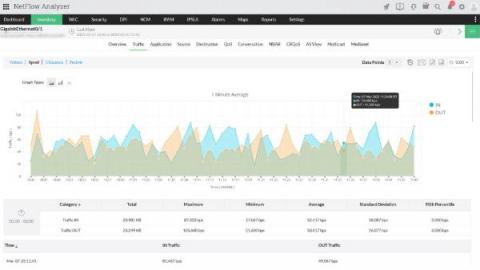
135,000 is the average number of endpoint devices connected to an enterprise network. The estimate is in a joint report from Adaptiva and the Ponemon Institute, along with several other surprising statistics: A common challenge facing IT professionals is gaining insight into the devices connected to their network. With so many devices being used by employees, managers and IT workers, a solution to categorize and analyze these devices in one spot is essential.