Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
Elastic Security Overview
Data Security and Privacy at Home
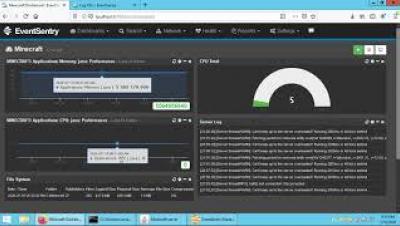
Monitoring a Minecraft server on Windows
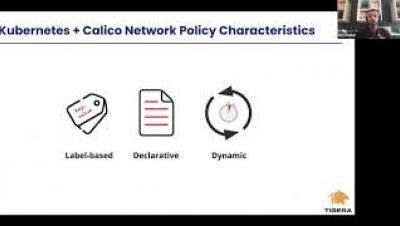
Calico and K8s Network Policies - An Overview and Comparison
Enable TLS with Let's Encrypt and the HAProxy Kubernetes Ingress Controller
The HAProxy Kubernetes Ingress Controller integrates with cert-manager to provide Let’s Encrypt TLS certificates. When it comes to TLS in Kubernetes, the first thing to appreciate when you use the HAProxy Ingress Controller is that all traffic for all services travelling to your Kubernetes cluster passes through HAProxy. Requests are then routed towards the appropriate backend services depending on metadata in the request, such as the Host header.
Reign in the Chaos of Security Threats with ChaosSearch
Kubernetes Security Best Practices You Must Know
Kubernetes (k8s) enables you to efficiently orchestrate container management, in the cloud or on-premises. As a whole, k8s provides many benefits, including features for self-healing, automated rollouts and rollbacks, load distribution, and scalability. However, k8s is a highly complex platform and requires extensive configuration.
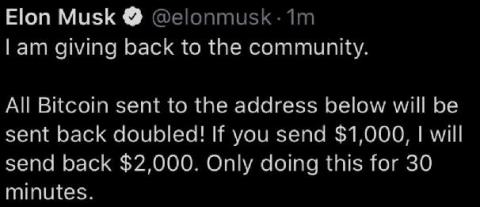
Unfolding the Twitter security incident
In case 2020 wasn’t dystopian enough, here’s some more unbelievable news. On July 15, 2020, social media giant Twitter admitted it fell victim to a security breach. The attackers targetted 130 Twitter accounts, including several belonging to high-profile individuals such as elected officials; former president Barack Obama; and business leaders including Bill Gates, Jeff Bezos, and Elon Musk.