Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
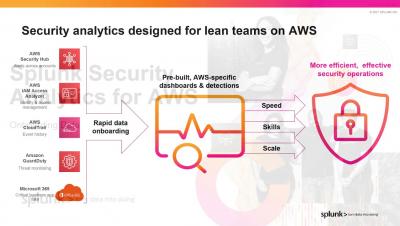
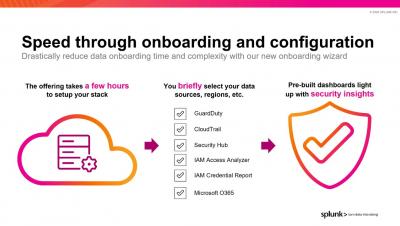
Detecting and Investigating Threats in Splunk Security Analytics for AWS
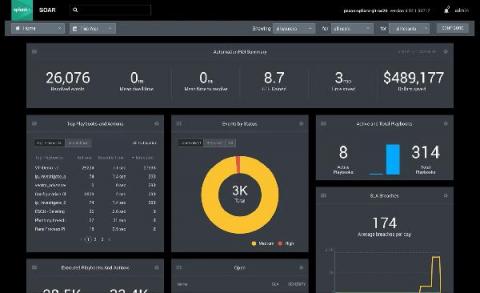
SOCtails Episode 4 - Respond Fast to Security Incidents with Automated Playbooks
How Biden's Executive Order on Improving Cybersecurity Will Impact Your Systems
President Joe Biden recently signed an executive order which made adhering to cybersecurity standards a legal requirement for federal departments and agencies. The move was not a surprise. It comes after a string of high-profile cyber-attacks and data breaches in 2020 and 2021. The frequency and scale of these events exposed a clear culture of lax cybersecurity practices throughout both the public and private sectors.
What's new in Sysdig - June 2021
Welcome to another monthly update on what’s new from Sysdig! Happy Pride month! We hope you are celebrating safely, in whatever manner you choose. It’s been over 50 years since the Stonewall riots, but we continue to fight for equality and justice. Love is love, and we’re sending you all of ours! Thank you to Marsha P. Johnson, Brenda Howard, and countless others for fighting for the freedom that many of us today enjoy.
7 Steps to Strengthen Your Security Posture
Learn more about your security posture and why it matters. Assess and strengthen your IT security posture with these critical steps.
The Increasing Popularity of Ransomware Amongst Cybercriminals
Cybercriminals are becoming increasingly savvy and ransomware attacks have soared over the last decade. A recent PwC UK Cyber Threat Intelligence report revealed a spike in cybersecurity incidents which have significantly affected many organisations that are already dealing with challenges caused by the pandemic.
Red Canary says 43% Lack Readiness to Notify Customers of a Security Breach
The phrase ‘stakeholder management” assumes that stakeholders are truly informed by alerts. However, managers can only send communications out, they cannot force people to address them. To ensure your stakeholders are engaged during an incident, it is vital to set up a defined communication process. Yet, a recent Red Canary report1 found that 43% of surveyed participants lack readiness to notify the public and/or its customers in the event of a security breach.
Introducing the World's First Modern Cloud-Based SecOps Platform: Splunk Security Cloud
To say that the past year presented its fair share of cybersecurity challenges to the InfoSec community would be a drastic understatement. The rapid migration to remote work at scale left 80% of CIOs unprepared, and SecOps teams struggled to confront the evolving threat landscape with disparate toolkits and skill sets. Not to mention that as more organizations shifted to hybrid and multi-cloud environments at scale, cloud complexity (and cloud-based threats) skyrocketed.
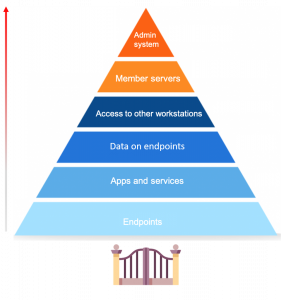
The role of endpoints in the security of your network
Endpoint security is a hot topic of discussion, especially now with so many businesses shifting to remote work. First, let’s define what endpoints are. Endpoints are end-user devices like desktops, laptops, and mobile devices. They serve as points of access to an enterprise network and create points of entry that function as gateways for malicious actors. Since end-user workstations make up a huge portion of endpoints, we’ll be focusing on their security.