Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
Using Splunk to Develop an Incident Response Plan
Five worthy reads: Unified endpoint management, a 360° look at organizational security
One of the most obvious effects of the digital age is the unprecedented advancements in technology. Thirty years back, driverless cars, missions to Mars, and AI-powered robots were pure science fiction. Today, all these things are close to being an everyday reality. And speaking of unparalleled innovations, who would’ve thought that the day would come when all the devices around us—from mobile devices to sensors and appliances—could exchange information amongst themselves.
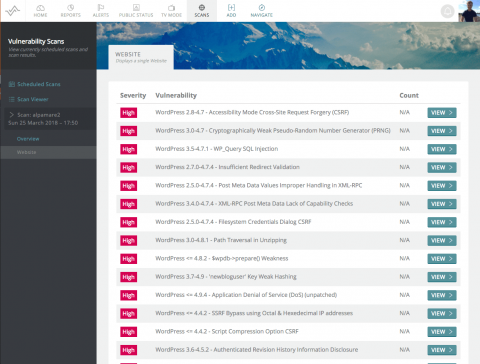
WordPress Security Scanning
With WordPress powering over 30% of the internet and a plugin ecosystem that allows anyone to write software which will execute code on your server, it’s no wonder that it’s become a popular target for hackers. As part of our Vulnerability Scanning service – which already checks for thousands of known software and configuration vulnerabilities for all major software products and operating systems – we now also test over 10,000 known WordPress vulnerabilities.
How to collect custom applications and services logs
ManageEngine SIEM Solution Introduces Office 365 Monitoring to Help Enterprises Ensure Business Continuity
Log360 Offers Health, Performance Monitoring for Office 365 Services.
The Value of Threat Intelligence Automation
The news is full of stories about the talent shortage in IT, especially in IT security. This shortage has created pressure on organizations to grow IT operations and to do that securely, all while having too few staff. Many are turning to threat intelligence to give their security analysts the tools they need to evaluate threats quickly and effectively. Essentially offering “Intelligence as a Service,” these tools enable organizations to benefit from the research of others.
Employ Unified Endpoint Management and Secure Endpoints
The Data Explosion and its Effect on Security
Data is exploding. The shift to digital business is driving a massive expansion in the volume of data that organizations produce, use, and store. It is also accelerating the velocity of data—that is, the data is changing more rapidly than ever before. Which in many ways is great—more data can bring more insight into customers, markets, and opportunities. But more data can also be a problem.