Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
File Sight Reported Files Read? What Happened?
We sometimes get requests from customers asking for help understanding a File Sight report. It often involves some user account is shown as having read 100’s of files very quickly. This post is to help explain what might have happened.
DevSecOps and Log Analysis: Improving Application Security
As time goes on, more and more organizations are abandoning the outdated waterfall development methodology for more practical and efficient Agile development practices. As this movement has occurred, development teams are moving faster than ever by employing Continuous Integration (CI) and Continuous Deployment (CD) practices that are serving to shorten development cycles and get new features into production with increasing speed.
Five worthy reads: Revolutionizing IT with artificial intelligence
Netflix recommends Stranger Things to you because it knows you like watching sci-fi thrillers. Tinder lets you swipe right into your next date because it’s learned your interests and partner preferences. Amazon keeps showing you Fitbit because you’ve spent a considerable amount of time browsing through the fitness and wellness category.
Penetration Testing from RapidSpike
The founders of RapidSpike built, managed, and successfully exited from a leading UK Security Company called RandomStorm before launching RapidSpike. One of the main areas that RandomStorm excelled in was Penetration Testing and the founders of RapidSpike have recently launched Pentest People to once again provide Penetration Testing services to the worldwide market.
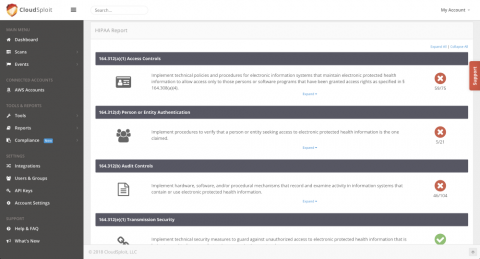
CloudSploit Compliance Scanning Scans AWS Infrastructure for Compliance with Privacy Standards
One of the most common business requirements data handlers face is the numerous data privacy standards present as industry standards. Each industry has their own variation, each with their own specific requirements — but regardless of the standard or the applied dataset, compliance is extremely important.
ManageEngine RecoveryManager Plus Adds Windows Server Backup and Restoration Capabilities
Automate Backups and Stay Insured Against Any Disaster, Security Mishap on Windows Servers.
Why do you need a SSL Certificate
First of all, what is SSL? It is short for Secure Sockets Layer. In simple words and without getting into too much technical details, adding a SSL certificate makes the connection more secure and much safer when you browse, buy and communicate online.