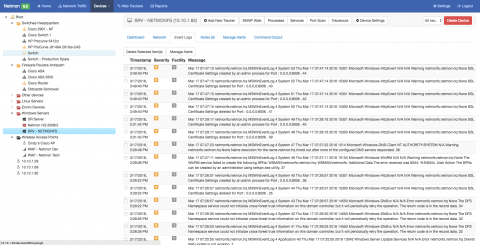
Configuring SYSLOG / Event Log on a Windows Device
Netmon’s complete Network Monitoring Solution can also be used as a centralized SYSLOG and Windows Event Log Server where you can quickly look through many Servers, Workstations or other Network devices’ SYSLOG and Event Log information without having to log into each individual device to see the same information.