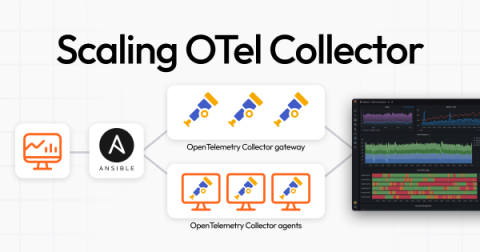
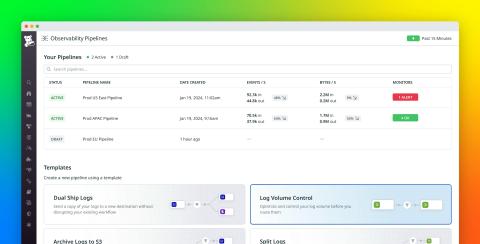
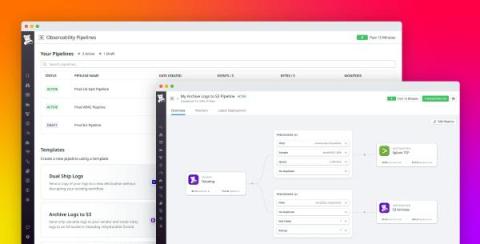
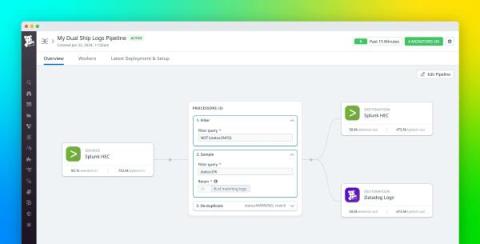
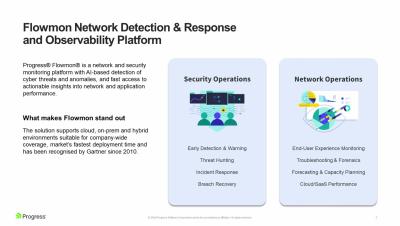
Top 10 Change Management Tools
Changes to software are inevitable and fundamental part of growth for any organization, however, change is often not straightforward. It can affect numerous aspects of a company and requires collaboration among all stakeholders. This is where change management tools come in to assist you with this. There’s currently a wide range of change management tools available, each providing benefits to specific scenarios and weaknesses to others.