Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
DDOS Attacks: How to Protect Yourself from the Political Cyber Attack
In the past 24 hours, funding website GiveSendGo has reported that they’ve been the victim of a DDOS attack, in response to the politically charged debate about funding for vaccine skeptics. The GiveSendGo DDOS is the latest in a long line of political cyberattacks that have relied on the DDOS mechanism as a form of political activism. There were millions of these attacks in 2021 alone.
Why you need Tigera's new active cloud-native application security
First-generation security solutions for cloud-native applications have been failing because they apply a legacy mindset where the focus is on vulnerability scanning instead of a holistic approach to threat detection, threat prevention, and remediation. Given that the attack surface of modern applications is much larger than in traditional apps, security teams are struggling to keep up and we’ve seen a spike in breaches.
Webinar Recap: Force Multiply Your Security Operations Teams with Cribl LogStream
We hosted a webinar a few weeks back on using Cribl LogStream to make your security operations more scalable, efficient, and cost-effective. The turnout was fantastic and, while we answered most of the audience’s questions live, we couldn’t get to all of them. So I’ll go through the questions we couldn’t get to and offer some answers. Along the way, I’ll also share the results of two polling questions we asked during the webinar.
ISO 31030: Evolving Expectations of Travel Risk Management
Organizations have had no choice but to continually adapt over the last few years, especially when it comes to protecting their traveling employees. In simpler times, organizations worried about missing or outdated passports, a rare airline food poisoning incident, weather delays, and turbulence. Today, increased canceled flights, thinning airline staff, closed borders, vaccine testing, and potential quarantining have stressed organizations looking to protect traveling employees.
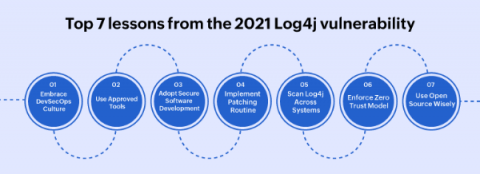
Top 7 lessons from the 2021 Log4j vulnerability
The Log4Shell (CVE-2021-44228) zero day vulnerability in the Java logging framework Log4j (versions 2.0 to 2.14.1) was revealed on December 9, 2021. The Apache Foundation assigned the maximum CVSS score of 10 to Log4Shell, as millions of servers and potentially, billions of devices came under risk. Security professionals around the world began patching the vulnerability, and scanning their systems to rule out any potential breach.
Collective Cybersecurity: A Shared Responsibility Model
The state of cybersecurity today is, in a word, catastrophic. Breaches have become endemic. Not only do they continue at dizzying rates, but they are actually increasing in frequency by the month. Why are things so bad? And why do businesses seem so helpless to make them better? Those are complicated questions without simple answers, of course – but I believe that a major part of the answer has to do with the fact that, at most organizations, security remains the domain of elite security teams.
JFrog Took Security to New Heights in 2021
3 Common Questions on Managing Your SD-WAN Network
How to Test Multi-Factor Authentication for Microsoft Teams
Our last blog introduced Multi-Factor Authentication (MFA) for synthetics and discussed how MFA works. Most of our customers use Microsoft Teams as their Go-To messaging and collaboration application. So in today’s article I will show you how to deploy the Teams Audio Video sensor in your environment with an MFA configuration. This will enable testing MFA while at the same time testing the performance of a Teams audio video conference.