How we keep N-central updated and secure
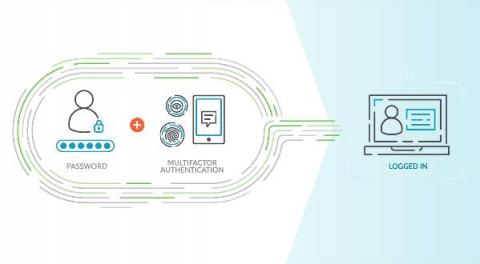
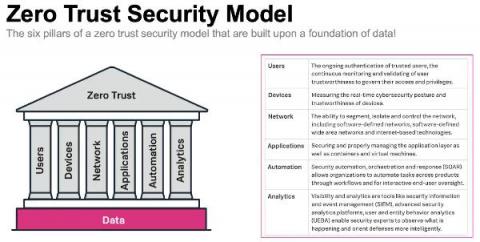
Following the security issues in the MSP market over the past 24 months, our customers, who are understandably concerned, have been asking what we do to keep the N-central® appliance (hosted or on-premises) updated and secure for them. I will do my best in this short article to outline how our engineering team keeps up with security. Please note this is valid as of the time of writing, but can change at any point.