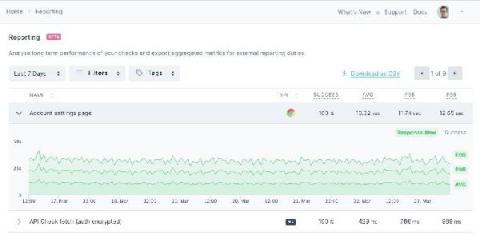
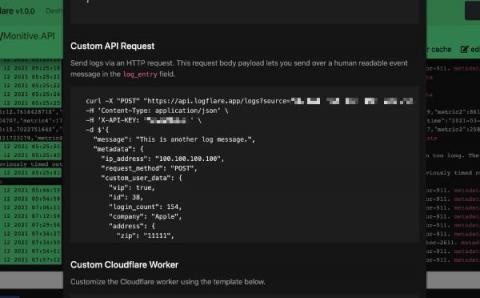
How to Add SaaS API Monitoring to LogicMonitor
SaaS or Software–as-a-Service is a term that describes many applications on the web today. Whether you’re using TurboTax (tax season is coming up) or Twitter, most people use SaaS platforms on a daily basis without even realizing it.