Data Tampering: A Comprehensive Guide
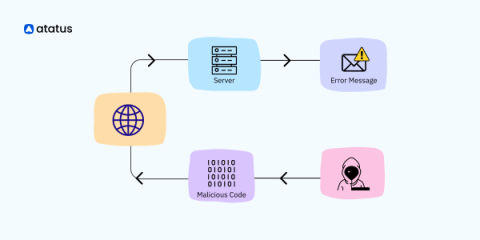
In an increasingly interconnected and data-driven world, where information shapes decisions and fuels innovation, the integrity of data has become paramount. However, lurking beneath the surface is a silent threat that can undermine trust, compromise systems, and wreak havoc on organizations: data tampering. In this post, we delve into the realm of data tampering, exploring the vulnerabilities, the reasons behind data tampering practices, and countermeasures against them.