Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
Fleet: Multi-Cluster Deployment with the Help of External Secrets
Fleet, also known as “Continuous Delivery” in Rancher, deploys application workloads across multiple clusters. However, most applications need configuration and credentials. In Kubernetes, we store confidential information in secrets. For Fleet’s deployments to work on downstream clusters, we need to create these secrets on the downstream clusters themselves.
Cloud Native Security for the Rest of Us
Why Scammers Want Your Information and How to Protect Yourself Online
The Evils of Data Debt
In this livestream, Jackie McGuire and I discuss the harmful effects of data debt on observability and security teams. Data debt is a pervasive problem that increases costs and produces poor results across observability and security. Simply put — garbage in equals garbage out. We delve into what data debt is and some long term solutions. You can also subscribe to Cribl’s podcast to listen on the go!
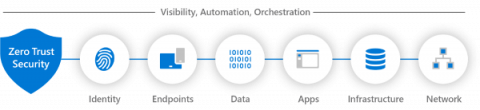
Applying Zero Trust to Data Centre Networks
Zero trust isn’t an approach that can be delivered by buying a single product that claims to provide it. Instead, it is an approach that needs to be understood and implemented in complementary ways across an organization’s IT systems. We recently hosted a webinar titled Applying Zero Trust to Data Centre Networks to provide guidance on how organizations can use zero trust to enhance the security of their IT systems. The webinar details are below, after a summary of the topics covered.
The 8 Best Practices for Reducing Your Organization's Attack Surface
Increases in attack surface size lead to increased cybersecurity risk. Thus, logically, decreases in attack surface size lead to decreased cybersecurity risk. While some attack surface management solutions offer remediation capabilities that aid in this effort, remediation is reactive. As with all things related to security and risk management, being proactive is preferred. The good news is that ASM solutions aren't the only weapons security teams have in the attack surface fight.
How Implementing Risk-Based Patch Management Prioritizes Active Exploits
Resistance to change is always present, especially if you think the processes you have in place are efficient and effective. Many organizations feel this way about their software management procedures until they have a security breach or incident and are left wondering where they went wrong. The reality is that most patch management programs are built on assumptions and recommendations, rather than facts about actively exploited vulnerabilities. Risk-based patch management is the answer to this issue.
Data security at scale: How IT modernization impacts cybersecurity and data access for the U.S. Department of Defense
As more and more of the public sector enact large-scale digital transformation initiatives, government organizations must find new ways to manage massive amounts of data securely while maintaining compliance. With new mandates from the Biden administration to enhance cybersecurity best practices in both the private and public sectors, organizations like the Department of Defense (DoD) face new challenges to their data management and communication practices.