Operations | Monitoring | ITSM | DevOps | Cloud
Alerting
What Is Microsoft Azure Sentinel and Why Is It Important?
Microsoft Azure Sentinel is an intelligent, next-generation security information and event management (SIEM) solution designed to detect threat anomalies. Azure Sentinel is also categorized as a security orchestration automated response (SOAR) service that expedites the incident detection and event response process for cybersecurity teams. Azure Sentinel provides an extra layer of security to protect critical resources across an organization.
Webhooks for Raygun Alerting - Create custom third-party integrations
Server Monitoring and Alerting
Server and IT infrastructure monitoring are critical to ensuring the performance and longevity of your client systems. Even more so, remote monitoring technology, in particular, has helped define the entire modern IT industry. In this post, we’re going to discuss several of the main monitoring concepts, including metrics, alerting, and monitoring, and why they are important.
Three communications best practices for incident handlers
The importance of well-managed communications when handling IT and security incidents cannot be overstated. If updates are not communicated in a timely and accurate manner, misunderstandings, misalignment, and costly errors will occur. Not to mention, resolution will be prolonged. And if highly sensitive information is communicated to those who should not be privy to such, then the risk of legal ramifications is high, as would be the damage.
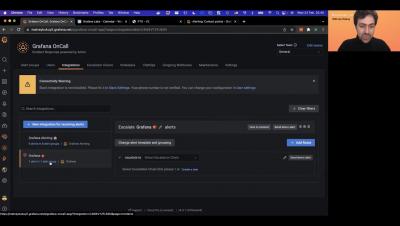
Getting started with Grafana OnCall
Customizing Error Pages (Nginx Ingress Controller)
The most common way to do it, which is part of the offical solution is to create a Docker image server capable of responding to any request with 404 content, except /healthz and /metrics. This could be an Nginx instance. /healthz should return 200 /metrics is optional, but it should return data that is readable by Prometheus in case you are using it for k8s metrics. Note: Nginx can provide some basic data that Prometheus can read. /returns a 404 with your custom HTML content.
Why Self-hosting Might not be a Good Choice for your Status Page
We all remember when Facebook, WhatsApp, and Instagram shut down in April of last year for a whole day. And while it was terrible for their company—it’s an educational moment for the rest of us to learn from. Facebook’s status page is self-hosted, and that puts their status pages at risk of the exact issue it’s designed to tell you about.
SIGNL4 in IT Security
Can Endpoint Protection Keep up With Modern Threats?
Endpoint protection is a security approach that focuses on monitoring and securing endpoints, such as desktops, mobile devices, laptops, and tablets. It involves deploying security solutions on endpoints to monitor and protect these devices against cyber threats. The goal is to establish protection regardless of the endpoint’s location, inside or outside the network.