Operations | Monitoring | ITSM | DevOps | Cloud
Blog
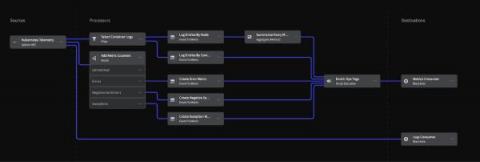
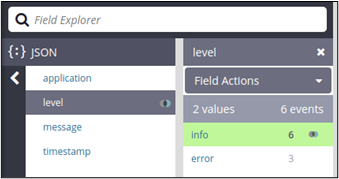
Understand Your Kubernetes Telemetry Data in Less Than 5 Minutes: Try Mezmo's New Welcome Pipeline
Most vendor trials take quite a bit of effort and time. Now, with Mezmo’s new Welcome Pipeline, you can get results with your Kubernetes telemetry data in just a couple of minutes. But first, let’s discuss why Kubernetes data is such a challenge, and then we’ll overview the steps.
Failure Metrics & KPIs for IT Systems
Into the Labyrinth: Revealing the Mantic Minotaur
Your Self-Managed Journey to Digital Resilience
Cloud storage for enterprises
Effective Logging in Node.js Microservices
Cloud repatriation: What's behind the return to on-premises?
Find out why cloud repatriation is on the rise — and what makes on-premises the ideal approach for some businesses. Over the last ten years, the cloud has been touted as a game-changer. But, like magpies, have we all jumped on the “shiny object syndrome” bandwagon? Spending on public cloud services continues to show strong growth, with Gartner forecasting that by the end of 2023, worldwide end user spending on public cloud services will total nearly $600 billion.
Microsoft Dynamics Monitoring: CRM Performance Optimization
Microsoft Dynamics empowers enterprises with efficient customer relationship management (CRM) and enterprise resource planning (ERP) capabilities. As organizations increasingly rely on the seamless functioning of Microsoft Dynamics to drive their core processes, the need for robust monitoring practices has become paramount. This is where Microsoft Dynamics Monitoring steps into the spotlight, bridging the gap between uninterrupted productivity and potential disruptions.
Azure Key Vault: A Comprehensive Overview
Azure Key Vault is Microsoft’s dedicated cloud service, designed to safeguard cryptographic keys, application secrets, and other sensitive data. In an era where digital security is paramount, it functions as a centralized repository. Here, sensitive data is encrypted, ensuring that only designated applications or users can access them. Imagine having a hyper-secure, digital vault where you can store all your essential digital assets.