Operations | Monitoring | ITSM | DevOps | Cloud
Incident Management
The latest News and Information on Incident Management, On-Call, Incident Response and related technologies.
Event-Driven Automation Panel
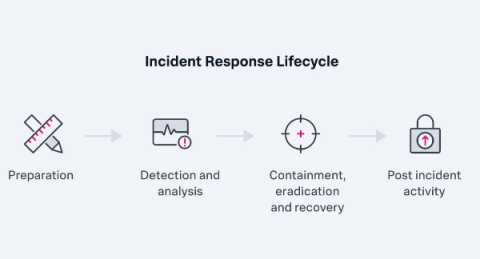
Incident Response Plans: The Complete Guide To Creating & Maintaining IRPs
8 Strategies for Reducing Alert Fatigue
Site Reliability Engineers (SREs) and DevOps teams often deal with alert fatigue. It's like when you get too alert that it's hard to keep up, making it tougher to respond quickly and adding extra stress to the current responsibilities. According to a study, 62% of participants noted that alert fatigue played a role in employee turnover, while 60% reported that it resulted in internal conflicts within their organization.
Supercharged with AI
Empowering your AIOps journey: Rediscovering the power of BigPanda University
We hope this message finds you well in your start to 2024. As pioneers in the field of AIOps, we understand that the landscape is ever-evolving, and staying ahead requires continuous learning. That’s why we’re thrilled to remind you of a particularly invaluable resource at your fingertips—BigPanda University.
The Catchpoint 2024 SRE Report - Five Key Takeaways
Ultima Release - xMatters
APAC Retrospective: Learnings from a Year of Tech Outages - Dismantling Knowledge Silos
As our exploration through 2023 continues from the second blog segment, “Mobilise: From Signal to Action”, one undeniable fact persists: Incidents are an unavoidable reality for organisations, irrespective of their industry or size. In the APAC region, a surge in regulatory enforcement has been observed against large corporations failing to meet service standards, resulting in severe penalties.
Mastering IT Alerting: A Short Guide for DevOps Engineers
$575 million was the cost of a huge IT incident that hit Equifax, one of the largest credit reporting agencies in the U.S. In September 2017, Equifax announced a data breach that impacted approximately 147 million consumers. The breach occurred due to a vulnerability in the Apache Struts web application framework, which Equifax failed to patch in time. This vulnerability allowed hackers to access the company's systems and exfiltrate sensitive data.