Exploring Form Submission and Custom Keyboards #short
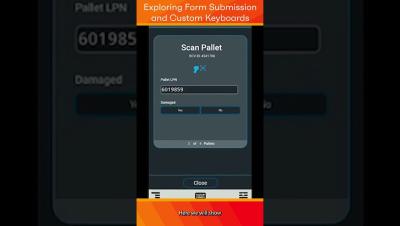
Upon form submission, a success message pops up. The demo showcases a green screen and data from previous transactions. It also highlights the creation of custom keyboards to launch forms, with the remaining transaction visible at the tile's bottom.