Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
Interview with Cybersecurity Specialist Mark Kerzner
For the newest instalment in our series of interviews asking leading technology specialists about their achievements in their field, we’ve welcomed Mark Kerzner, software developer and thought leader in cybersecurity training who is also the VP at training solutions company, Elephant Scale. His company has taught tens of thousands of students at dozens of leading companies. Elephant Scale started by publishing a book called ‘Hadoop Illuminated‘.
How we keep N-central updated and secure
Following the security issues in the MSP market over the past 24 months, our customers, who are understandably concerned, have been asking what we do to keep the N-central® appliance (hosted or on-premises) updated and secure for them. I will do my best in this short article to outline how our engineering team keeps up with security. Please note this is valid as of the time of writing, but can change at any point.
Applied AI for fraud prevention and detection
Securing AWS IAM with Sysdig Secure
Last year’s IDC’s Cloud Security Survey found that nearly 80 percent of companies polled have suffered at least one cloud data breach in the past 18 months.
Kubernetes security issues: An examination of major attacks
In a never-ending game of cat and mouse, threat actors are exploiting, controlling and maintaining persistent access in compromised cloud infrastructure. While cloud practitioners are armed with best-in-class knowledge, support, and security practices, it is statistically impossible to have a common security posture for all cloud instances worldwide. Attackers know this, and use it to their advantage. By applying evolved tactics, techniques and procedures (TTPs), attackers are exploiting edge cases.
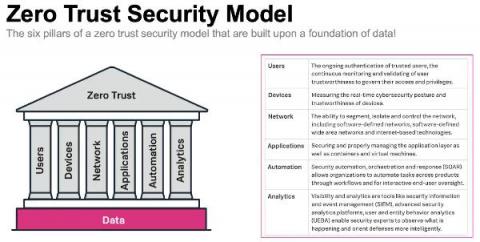
A Zero Trust Security Approach for Government: Increasing Security but also Improving IT Decision Making
Public sector organisations are in the middle of a massive digital transformation. Technology advances like cloud, mobile, microservices and more are transforming the public sector to help them deliver services as efficiently as commercial businesses, meet growing mission-critical demands, and keep up with market expectations and be more agile.
Hunting for threats in multi-cloud and hybrid cloud environments
Remote work and its lasting impact: What our global research uncovered
The COVID-19 pandemic has not only had a profound impact on everyone across the globe; it has also fundamentally changed the way organizations function. We are nearing one and a half years since remote work became the norm and organizations had to adapt to this new mode of working almost overnight. This rapid transition wouldn’t have been possible without the massive technology, workflow, and process upgrades undertaken by IT departments.
Secure your infrastructure in real time with Datadog Cloud Workload Security
From containerized workloads to microservice architectures, developers are rapidly adopting new technology to scale their products at unprecedented rates. To manage these complex deployments, many teams are increasingly moving their applications to third party–managed services and infrastructure, trading full-stack visibility for simplified operations.